AI helps design underwater gliders that swim like fish
Underwater robots called gliders are often used to explore the ocean, collecting important data like water temperature, salt levels, and information about currents.
These gliders...
Wax-powered cooling system could keep space electronics from overheating
A team of researchers is taking an innovative approach to keeping electronics cool in space—using wax.
Led by Professor Mickey Clemon from the University of...
What is the optimal setting for your air conditioner
Ahh, summer, a time of vacations at the beach or mountains—and sky-high electricity bills as your air conditioner labors against the heat and humidity.
But...
Ultra-stretchy smart foam could power the future of wearable tech
Scientists in China have created a new kind of soft, stretchable foam that could transform how we track body movement, monitor health, and interact...
Smart sticky surface could revolutionize micro-LED displays
Researchers at South Korea’s Pohang University of Science and Technology (POSTECH) have created a groundbreaking material that can stick to tiny objects like micro-LED...
How a pizza-sized robot and VR could change lunar missions
Someday, robots might crawl across the moon helping astronauts build science labs and even future homes—and some of the early work to make that...
New quantum material could make electronics 1,000 times faster
Scientists at Northeastern University have made a major breakthrough that could revolutionize how fast and powerful our electronic devices become.
By learning how to switch...
Tiny satellite could make quantum communication a reality
A small satellite about the size of a shoebox has been launched into space to test exciting new quantum communication technology.
Called QUICK³, the satellite...
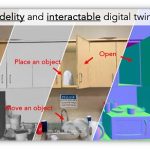
From phone video to virtual reality: AI turns real rooms into interactive 3D spaces
Imagine taking a short video of your kitchen with your phone, and then being able to walk through a detailed 3D version of it—opening...
Smart memory devices that melt away in water could help tackle e-waste
As technology becomes a bigger part of our everyday lives, so does the problem of electronic waste.
From smartwatches and fitness trackers to medical patches...