Simple changes could cut AI energy use by 90%
Artificial intelligence (AI) tools like ChatGPT have become hugely popular around the world. Every day, people use them for writing, translating, answering questions, and...
Replying to the wrong text could cost you, data security expert says
Don't believe everything you read—especially if it's a text message like these:
"Notice: Your vehicle was identified as having an unpaid toll. Click now...
Robot performs first realistic gallbladder surgery without human help—and learns as it
In a groundbreaking moment for medicine and artificial intelligence, a surgical robot has successfully performed a realistic portion of a gallbladder removal without any...
Scientists unlock the power of quantum computing for everyone
Quantum computers are known for their incredible speed and power—but until now, they’ve had one big problem: they could only run one task at...
Next-gen optical chips take shape with Lego-like precision
A team of researchers from the University of Strathclyde has taken a major step forward in developing next-generation optical chips—tiny devices that control light...
AI helps finds a hidden cause of Alzheimer’s disease and new treatment
A new study from the University of California San Diego has uncovered a hidden cause of Alzheimer’s disease that may lead to a new...
AI predicts sudden heart death with higher accuracy than doctors
A powerful new artificial intelligence system has shown it can predict who is at risk of sudden cardiac death far better than current medical...
AI helps design underwater gliders that swim like fish
Underwater robots called gliders are often used to explore the ocean, collecting important data like water temperature, salt levels, and information about currents.
These gliders...
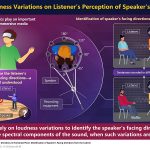
How sound tells us where someone is facing—and why it matters in virtual reality
Have you ever wondered how we can tell which direction someone is facing just by hearing their voice?
A group of researchers in Japan recently...
New material could revolutionize low-power memory and 6G devices
Imagine your phone or computer lasting much longer on a single charge, storing more data, and running more smoothly.
Thanks to a new breakthrough from...